TFW Software
Software for friction welders
Hidden Features
Some applications contain hidden features. They are not secret and are not malicious. They are not widely known and not usually known to customers for one or more of the following reasons:
- They provide functionality that is intended for debugging or testing and are not generally useful to customers.
- They may have limitations or bugs.
- They are not documented (except here).
Some of these features are described below. The list is not exhaustive and more may be added in future.
Export View
The Export View feature is accessed by the key combination .
It exports the last active view of the application to a bitmap on the clipboard. The bitmap may be subsequently pasted into another application.
Most application views are composed of more than one internal view and there may be more than one application view active at a time. Therefore, there are often several views to choose when you initiate the export command. When this is the case, the application presents a list of the active views and allows you to choose which one you want to export.
Note: it is not always possible to export a view (especially when it is an embedded partial view). Depending on the state of the application, it may be wholly or partly hidden or may not have all the necessary data connections available.
This feature is provided in the following applications:
- Welder
- Weld Playback
- DeFlash
- TFW Log Viewer
- User Manager
- Message Editor
Send Log
The Send Log feature is accessed by the key combination .
It adds a 'fake' Fatal entry into the log. That, in turn, will cause the logging infrastructure to email the log to whatever log recipients are configured. Obviously emailing will only work if the PC has an Internet connection that will allow it.
This feature is provided in the following applications:
- Welder
- Weld Playback
- DeFlash
- TFW Log Viewer
- User Manager
- Message Editor
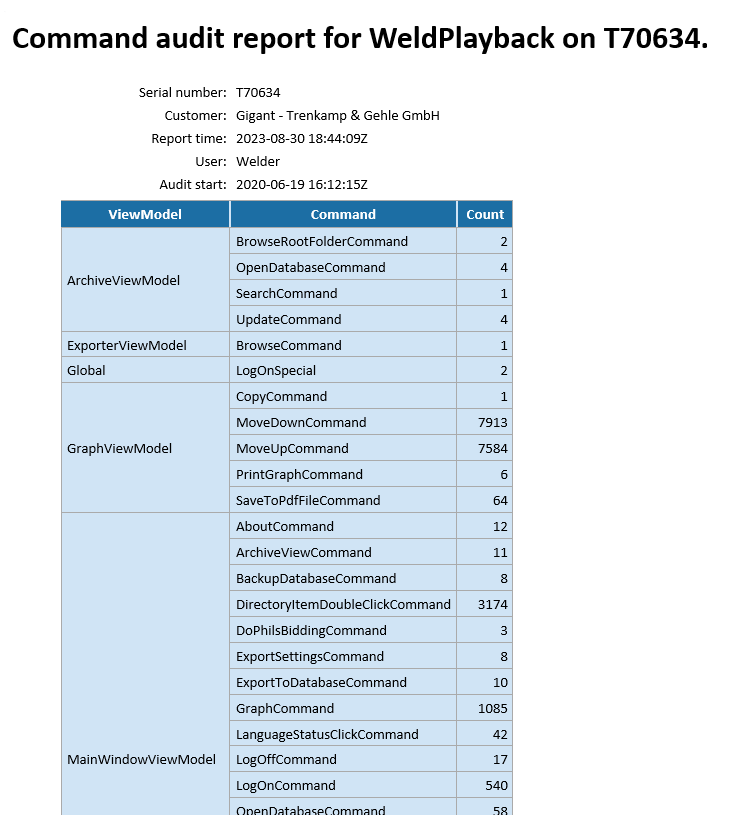
Command Auditing
Several applications have internal command auditing. This keeps a usage count of all commands executed in the software. In this contet, a command is a concept implemented in software to carry out a specific action. Many such commands are directly related to actions taken by the user, such as Save File or Send Parameters but others will be internal to the software.
Keeping a count of command usage gives an indication of which features of the software are most used and can guide future development and refinement of the user interface. The application (according to its configuration) will email audit reports on a regular basis, if the PC has an Internet connection that will allow it. It also has hidden features related to the audit, as follows.
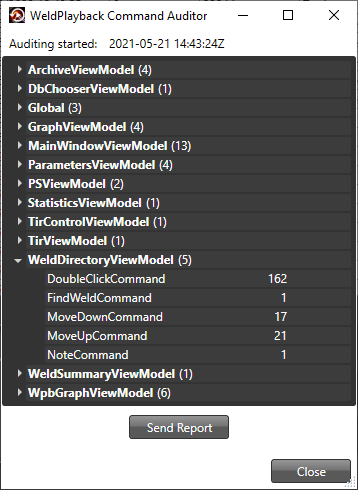
Show Audit Counts
The Show Audit Counts feature is accessed by the key combination . The logged-in user must be a member of the TFW Personnel group to enable the feature. The application shows a window with a view of the command counts.
Reset Audit Counts
The Reset Audit Counts feature is accessed by the key combination . The logged-in user must be a member of the TFW Personnel group to enable the feature. The application resets all the command counts to zero.
Send Audit Report
The Send Audit Report feature is accessed by the key combination . The feature works with any user or no user logged in. The application emails the audit report if the PC has an Internet connection that will allow it.